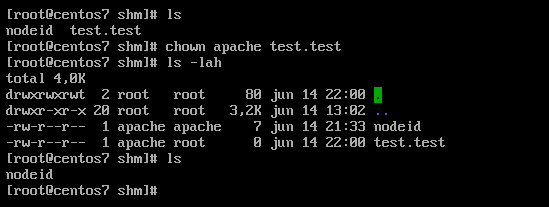
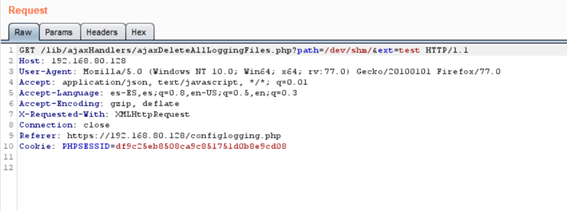
Background: Protected Processes in Windows
Windows implements a security mechanism called “Protected Processes” that prevents even administrator-level users from tampering with critical system processes. Many system processes, antivirus solutions, and EDRs use this protection level, including Windows Defender.
Understanding Process Access Rights
When attempting to open a handle to a process using the OpenProcess Windows API function, different access rights can be requested. For protected processes, most access rights are denied by default, even with administrator privileges.